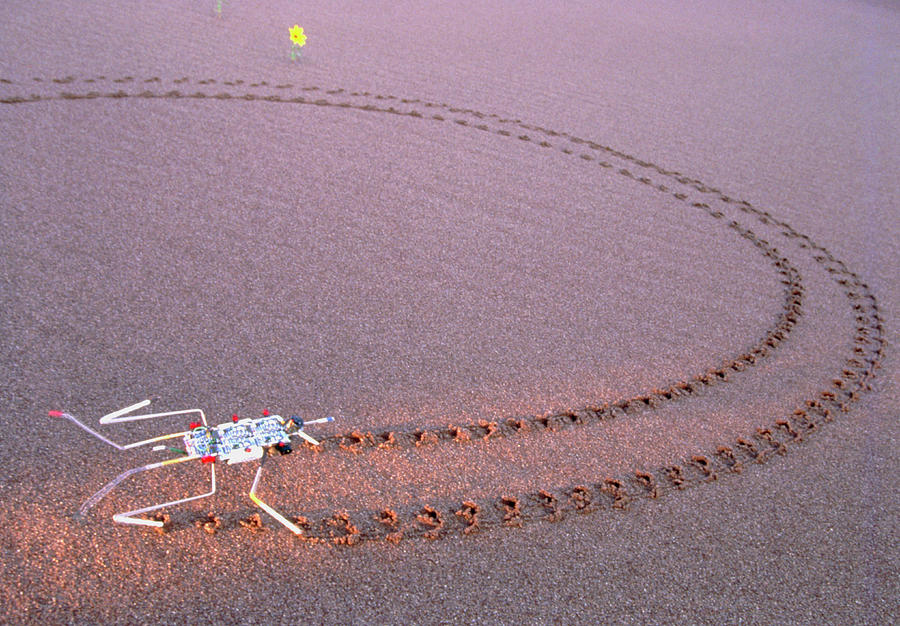
It was the early nineties when I first saw the photograph of a small robot wandering the desert. I would go on to buy the Robo Sapien book which featured photographs from the same shoot, along with more from Peter Menzel. Iconic. Simple. Inspiring and, most of all, achievable.
Robotics in the 1980s and 1990s were incredibly complex and costly. Significant computing power and sensor tech was needed to move a limb. The idea of walking robots was a dream, to some, a fantasy. Rodney Brooks had made some advances with Genghis and Attila. But these were still tens of thousands of dollars. Such robots were available to grad students and researchers, but out tantalizingly of reach for the rest of us.
Enter Mark Tilden. The robot in the Menzel’s photograph, and the rest of Tilden’s menagerie in the 1990s, had a price tag of a few hundred dollars. Many were built from scrap parts and recycled electronics. This allowed for rapid prototyping, which in turn facilitated rapid innovation. End result? Simple robots that worked. Inexpensive robots that walked.
The real lesson I took from Tilden, which I applied both when I built his style of robots and when I designed IT systems, was how to copy an idea. It works like this:
- Identify the features are providing the value
- Deconstruct those into underlying principles and tasks
- Emulate those tasks using the people and technology you have on hand
- Act on those tasks to reproduce the effect, prototype and iterate, to develop your own way of providing the value
Tilden called his process biomimicry because the stated goal was to mimic biological systems. More broadly, applying Tilden’s process to my framework, you can envision the steps as follows:
- Identify = Insects walk with legs controlled by a core set of neurons oscillating in a loop
- Deconstruct = an oscillator with feedback
- Emulate = two, four, or six inverter oscillators, or in BEAM nomenclature, Bicore, Quadcore, or Hexcore
- Act = Unibug 1.0, seen in the photograph below
I wager this is the same process Tilden used to build unthinkable robots for a fraction of the cost using parts he had lying around. Meanwhile, in security, we’re challenged to build security capabilities with little budget using what we have on hand. This is where my IDEA method shines.
Implementing any capability reference model or framework is beyond the capacity of most organizations. So? Don’t.
In October 2019, I was in Haifa visiting the Technion. There I saw robots which mimicked the snakes which populate the deserts of Israel. The same movements that facilitate movement through the deserts of Israel are useful in navigating the rubble of fallen buildings and industrial accidents, in order to find survivors. My mind was instantly transported back to Mark Tilden and his spare-part creatures. It struck me that Alon Wolf’s bio-inspired snakes are the technological children of Tilden’s early experiments.
By following a process that closely mirrors my IDEA model, the engineers at the Technion had created a simple, efficient, and focused device which literally saves lives. They identified an unlikely source of inspiration and deconstructed that down to its most iconic element: the serpentine wiggle. They iterated until they were able to emulate this wiggle. Then they put their invention into action: rescuing folks who would otherwise perish.
We can do the same thing in our cyber security work.
Select your reference model. (Say, for an Identity and Access Management or IAM platform.) Use the process above to see where the value is coming from. (Let’s say, on-boarding and off-boarding.) Deconstruct these down to a few core objectives. Then, see what’s available in your organization in terms of tools and techniques. Run inexpensive and quick pilots to try out the ideas and form a plan.
Don’t act on all the things. Act on the right things.
This article is part of a series on designing cyber security capabilities. To see other articles in the series, including a full list of design principles, click here.
Posted by